How to effectively and standardize the management of operators and operation behavior is the core of data center operation and maintenance management. Palladium's unified security management and comprehensive audit system solution adopts the management idea of "prevention in advance, control in process and post audit". From the perspective of how to reduce operational risk, take people, operation and technology as the management core.
Through the construction of Palladium unified safety management and comprehensive audit system, the following effects are achieved:
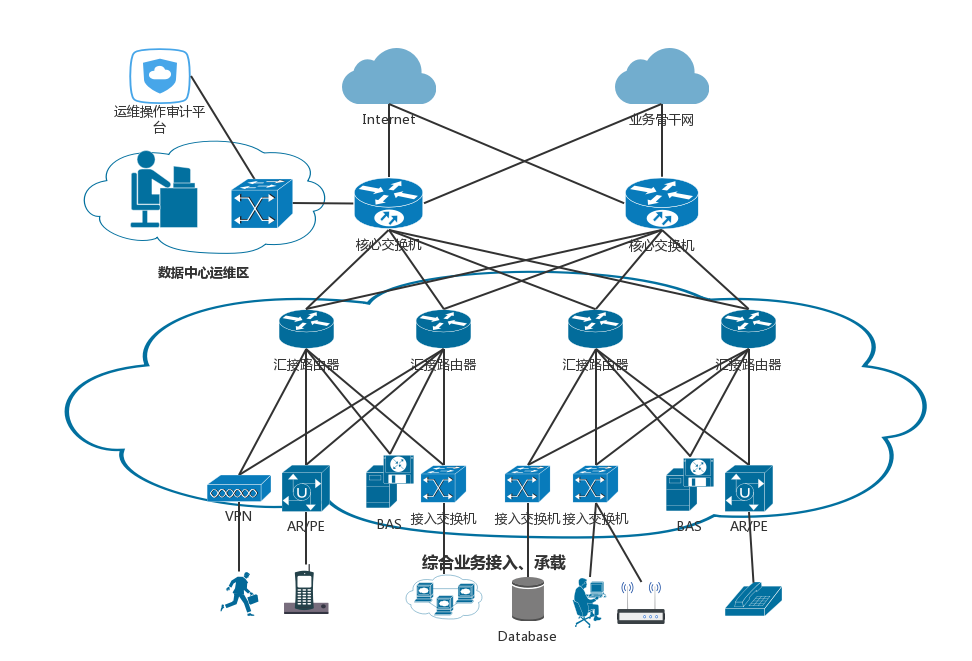
one Provide users with unified access and platform for operation and maintenance;
two Realize the centralized control and management of account number, authentication, authorization and audit of business support system, DCN network operation management system, operating system, database, network equipment and other IT resources;
three Realize centralized and role-based master-slave account management, and realize fine-grained permission allocation and management of role attribute level;
four Realize centralized identity authentication and access portal;
five Realize centralized access authorization, access control based on centralized control security policy and role authorization management;
six Realize centralized security audit management, collect and record users' use of key and important resources of business support system;
seven Meet the requirements of compliance audit and operation and maintenance management.
Deployment mode
Program advantages
Mature and stable
More than ten years of market verification and technology accumulation, and a large number of successful cases have been deployed in complex application production environment, especially many operators and financial cases;
The equipment is easy to maintain and manage. It has obvious advantages in the case of multi machine deployment. It has participated in the deployment of large projects with 30 equipment deployment, 14 equipment for cluster management, 2000 concurrent users and 10000 asset authorization management;
There are many industry cases of operators: China Mobile Group Zhejiang Co., Ltd., China United Communications Co., Ltd. Zhejiang branch, China Telecom Co., Ltd. Shanghai branch and China Telecom Co., Ltd. Anhui Branch.
Safe and reliable
At the same time, two sets of unified operation and maintenance platforms with independent applications and complete functions are provided. The device HA can achieve real-time synchronization of configuration and audit log;
Strong adaptability to network environment, realize green deployment, do not change the original network topology, support cluster deployment and cross network segment deployment;
The system development and update shall follow the safety software development life cycle process to realize version management, and each iterative upgrade shall ensure that the best practices are met.
modern techniques
Support local authentication, ad domain authentication, radius authentication, fingerprint authentication, wechat authentication, SMS authentication, etc., with the most complete identity authentication methods in the industry;
The system login strategy of users can be set, including limiting login IP, login time period, port, account, etc., to ensure that new users can access the background resources they have permissions and realize controllable operation and maintenance;
Support the alarm and blocking of high-risk commands, and effectively control the risks caused by misoperation and high-risk operation in operation and maintenance;
Unified management of in band and out of band operation and maintenance, the only mainstream KVM over IP products in the industry that simultaneously support Avocent, Raritan, aten, etc;
The original database operation and maintenance audit platform covers mainstream commercial database enterprise applications and operation and maintenance operations.